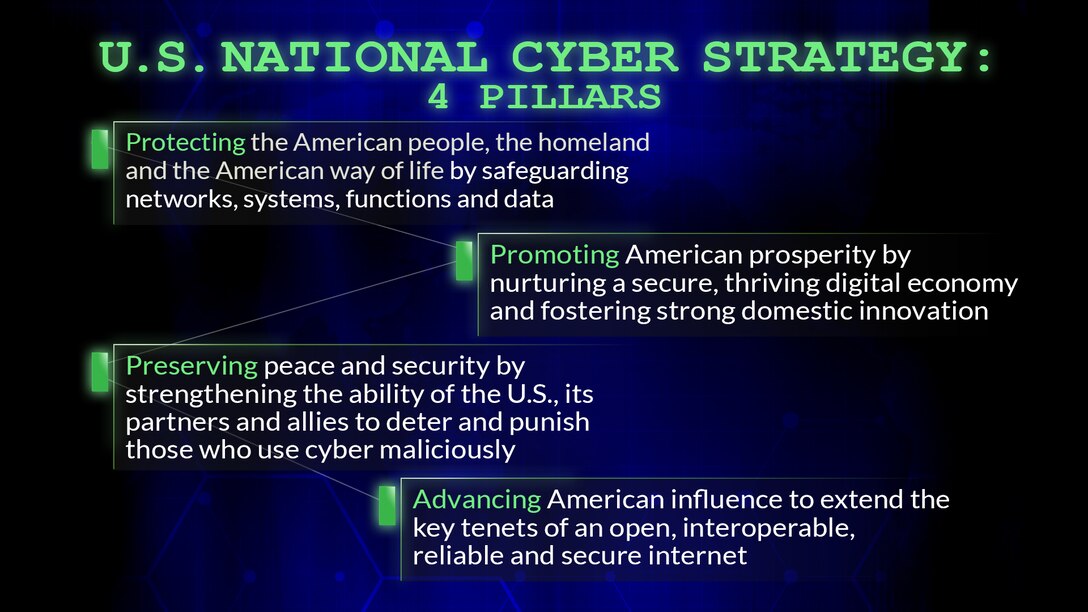
Strategi keamanan siber nasional pdf, or national cybersecurity strategy, plays a crucial role in safeguarding countries from digital threats. In this overview, we will explore the key components of such a strategy, the importance of international cooperation, and real-life case studies that provide valuable insights.
Brace yourself for a captivating journey into the world of cybersecurity.
Introduction to Cybersecurity Strategy
Cybersecurity strategy refers to the comprehensive plan and approach adopted by a nation to protect its digital infrastructure and assets from cyber threats. In today’s interconnected world, where information and communication technologies (ICT) play a crucial role, cybersecurity strategy has become a vital component of national security.
The Importance of Cybersecurity Strategy in National Security
A strong cybersecurity strategy is of paramount importance in maintaining national security. It ensures the protection of critical information and infrastructure, including government networks, defense systems, financial institutions, and essential services such as energy, transportation, and healthcare. By safeguarding these critical assets, a nation can prevent disruptions, vulnerabilities, and potential attacks that could have severe consequences on its economy, public safety, and overall stability.
The Role of Cybersecurity Strategy in Protecting Critical Infrastructure
Critical infrastructure refers to the systems and assets that are essential for the functioning of a society and economy. These include power grids, communication networks, water supplies, transportation networks, and financial systems, among others. Cybersecurity strategy plays a crucial role in protecting these critical infrastructures from cyber threats, which have the potential to cause significant damage and disruption.
It involves implementing robust security measures, conducting regular risk assessments, developing incident response plans, and fostering collaborations between the government, private sector, and other stakeholders.
Challenges and Threats Faced by Nations in Cyberspace
Nations face a myriad of challenges and threats in the cyberspace domain. One of the primary challenges is the constantly evolving nature of cyber threats, which require nations to continuously adapt and update their cybersecurity strategies. The increasing sophistication of cyber attacks, such as advanced persistent threats (APTs) and ransomware attacks, poses significant risks to national security.
Moreover, the interconnectedness of cyberspace makes it challenging to attribute attacks to specific actors, further complicating the response and deterrence efforts.The threats faced by nations in cyberspace include state-sponsored attacks, cyber espionage, intellectual property theft, and the disruption of critical services.
Nation-states, terrorist organizations, criminal syndicates, and hacktivist groups are among the actors that pose these threats. The consequences of successful cyber attacks can range from financial losses to compromised national security and even loss of life.In conclusion, cybersecurity strategy is a vital component of national security, as it protects critical infrastructure, mitigates threats in cyberspace, and ensures the stability and resilience of a nation.
Radika karya utama dalam perlindungan keamanan siber adalah legislasi dan otoritas eksekutif. Legislasi yang dibuat merupakan instrumen hukum yang memberikan dasar bagi pemerintah untuk melindungi keamanan siber negara. Otoritas eksekutif, yaitu lembaga atau individu yang memiliki wewenang untuk melaksanakan kebijakan-kebijakan terkait keamanan siber, bertanggung jawab dalam mengelola dan menjaga keamanan siber negara.
Lebih banyak informasi mengenai radika karya utama dalam perlindungan keamanan siber dapat Anda temukan di sini .
By understanding the importance of cybersecurity strategy and the challenges faced, nations can develop robust strategies to safeguard their digital assets and maintain a secure cyberspace.
Key Components of a National Cybersecurity Strategy
The development of a comprehensive national cybersecurity strategy is crucial in today’s digital age. Such a strategy should encompass various key components to effectively address the challenges posed by cyber threats.
1. Cybersecurity Governance
To ensure effective implementation of cybersecurity measures, a national strategy should establish a clear governance framework. This includes defining the roles and responsibilities of government agencies, private sector organizations, and other stakeholders involved in cybersecurity. A centralized authority can help coordinate efforts, set standards, and provide guidance to enhance the overall cybersecurity posture of the nation.
2. Risk Assessment and Management
A national cybersecurity strategy should incorporate a robust risk assessment and management framework. This involves identifying and evaluating potential threats and vulnerabilities, assessing the impact of cyber incidents, and implementing proactive measures to mitigate risks. Regular risk assessments can help identify emerging threats and ensure that cybersecurity strategies remain adaptive and up-to-date.
3. Incident Response and Recovery, Strategi keamanan siber nasional pdf
An effective national strategy should include provisions for incident response and recovery. This involves establishing mechanisms to detect, respond to, and recover from cyber incidents in a timely manner. Collaboration between government agencies, private sector organizations, and other stakeholders is vital to ensure a coordinated and efficient response to cyber threats.
4. Public Awareness and Education
Raising public awareness and promoting cybersecurity education is a crucial component of a national strategy. By educating individuals about cyber risks and best practices, they can become active participants in safeguarding their own digital lives. Public awareness campaigns, cybersecurity training programs, and initiatives to enhance digital literacy can empower individuals to make informed decisions and contribute to a safer cyber environment.
5. Research and Development
Investing in research and development is essential for staying ahead of constantly evolving cyber threats. A national cybersecurity strategy should allocate resources for research and development activities aimed at developing innovative technologies, tools, and techniques to enhance cybersecurity capabilities. Collaboration between academia, industry, and government can foster innovation and drive advancements in the field of cybersecurity.
6. International Cooperation
Cyber threats are not confined within national borders, making international cooperation a vital component of any national cybersecurity strategy. Collaborating with other nations, sharing threat intelligence, and participating in international cybersecurity initiatives can help create a united front against cyber threats.
Establishing bilateral and multilateral agreements can facilitate information sharing, capacity building, and joint efforts to combat cybercrime.
Importance of Public-Private Partnerships in Implementing Cybersecurity Strategies
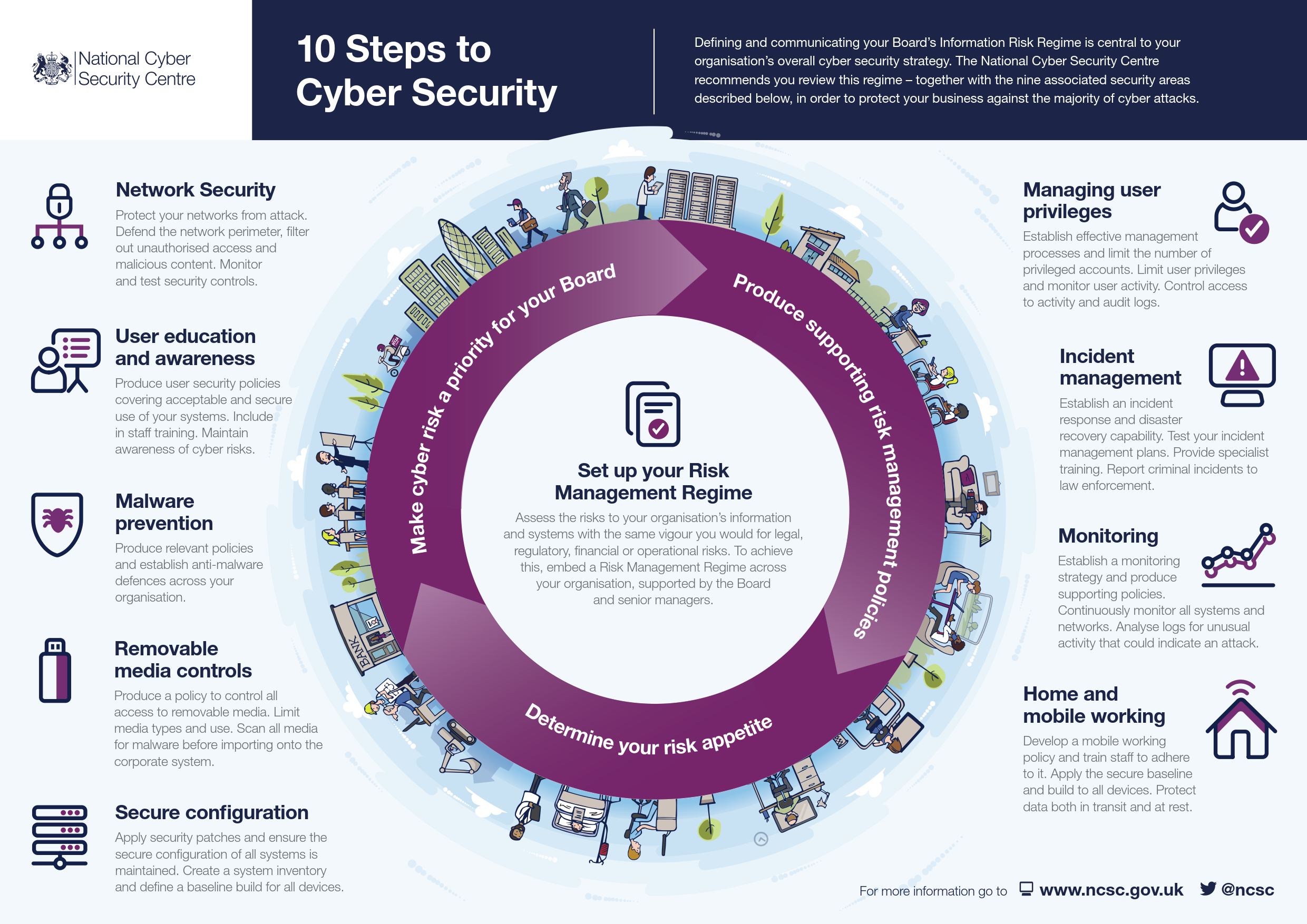
Public-private partnerships play a crucial role in implementing cybersecurity strategies. The collaboration between government entities and private sector organizations brings together complementary expertise, resources, and perspectives to tackle cyber threats effectively.
1. Enhanced Information Sharing
Public-private partnerships facilitate the sharing of vital information related to cyber threats, vulnerabilities, and best practices. This exchange of information enables both sectors to stay informed about emerging threats and adopt proactive measures to mitigate risks.
2. Coordinated Response and Recovery
In the event of a cyber incident, public-private partnerships enable a coordinated response and recovery effort. By working together, government entities and private sector organizations can share resources, expertise, and technologies to minimize the impact of cyber attacks and expedite the recovery process.
Rekayasa sosial adalah suatu metode yang digunakan untuk mempengaruhi dan memanipulasi perilaku manusia dengan menggunakan teknik-teknik psikologis. Tujuannya adalah untuk mengubah pola pikir dan tindakan individu atau kelompok sesuai dengan kepentingan pihak yang melakukan rekayasa sosial. Contohnya adalah kampanye politik yang menggunakan pesan-pesan yang dirancang secara khusus untuk mendapatkan dukungan dari masyarakat.
Lebih lanjut mengenai rekayasa sosial dapat Anda baca di sini .
3. Access to Specialized Skills and Technologies
The private sector often possesses advanced technologies and specialized skills that can enhance a nation’s cybersecurity capabilities. Public-private partnerships provide the government with access to these resources, enabling the implementation of state-of-the-art cybersecurity solutions and strengthening the overall cybersecurity posture.
Role of Legislation and Regulation in Cybersecurity Strategy
Legislation and regulation play a crucial role in supporting and enforcing cybersecurity strategies. They provide a legal framework to ensure compliance, establish standards, and promote accountability in the realm of cybersecurity.
1. Establishing Legal Frameworks
Legislation enables the establishment of legal frameworks that define cyber offenses, penalties, and enforcement mechanisms. This creates a deterrent against cybercriminal activities and ensures that individuals and organizations are held accountable for their actions.
2. Promoting Compliance and Best Practices
Regulation can mandate cybersecurity measures and standards that organizations must adhere to. This promotes compliance with cybersecurity best practices and ensures a baseline level of security across critical sectors. By setting minimum requirements, regulation helps protect against cyber threats and enhances overall cybersecurity resilience.
3. Facilitating Information Sharing and Collaboration
Legislation can enable the sharing of cybersecurity-related information between government entities and private sector organizations. This facilitates collaboration, enables a quicker response to cyber threats, and enhances collective cybersecurity efforts.
4. Supporting Law Enforcement and Investigation
Legislation provides the legal framework for law enforcement agencies to investigate cybercrimes, gather evidence, and prosecute cybercriminals. This ensures that cybercriminals are held accountable for their actions and helps deter future cyber threats.In conclusion, a comprehensive national cybersecurity strategy should encompass key components such as cybersecurity governance, risk assessment and management, incident response and recovery, public awareness and education, research and development, and international cooperation.
Public-private partnerships are vital for implementing cybersecurity strategies, as they enable enhanced information sharing, coordinated response and recovery, and access to specialized skills and technologies. Legislation and regulation play a crucial role in supporting cybersecurity strategies by establishing legal frameworks, promoting compliance and best practices, facilitating information sharing and collaboration, and supporting law enforcement and investigation efforts.
International Cooperation in Cybersecurity
International cooperation plays a vital role in addressing cyber threats in today’s interconnected world. Cyber attacks are not confined by borders and can impact individuals, organizations, and even nations on a global scale. Therefore, collaborative efforts are necessary to combat these threats effectively.
Existing International Frameworks and Agreements for Cybersecurity Cooperation
Several international frameworks and agreements have been established to promote cooperation in the field of cybersecurity. These frameworks aim to facilitate information sharing, capacity building, and the development of common strategies to respond to cyber threats. Some notable examples include:
- The Budapest Convention on Cybercrime: This treaty, adopted by the Council of Europe, aims to harmonize national laws related to cybercrime and enhance international cooperation in investigating and prosecuting cybercriminals.
- The United Nations Group of Governmental Experts (UN GGE) on Developments in the Field of Information and Telecommunications: This group brings together experts from various countries to discuss and develop norms, rules, and principles for responsible state behavior in cyberspace.
- The International Telecommunication Union (ITU) Global Cybersecurity Agenda (GCA): The ITU GCA promotes international cooperation and collaboration among governments, industry, and other stakeholders to build confidence and security in the use of information and communication technologies.
- The Five Eyes Alliance: This intelligence alliance between the United States, United Kingdom, Canada, Australia, and New Zealand focuses on signals intelligence and includes cooperation in cybersecurity.
Challenges and Barriers to Effective International Cybersecurity Cooperation
While international cooperation in cybersecurity is crucial, it is not without its challenges and barriers. Some of the main obstacles include:
- Differing legal frameworks and jurisdictional issues: Countries have different laws and regulations regarding cybersecurity, making it difficult to coordinate investigations and share information across borders.
- Lack of trust and information sharing: Sharing sensitive information between nations can be challenging due to concerns over national security and the potential misuse of shared data.
- Political tensions and conflicts: Political disputes and conflicts between countries can hinder collaboration in cybersecurity, as trust and cooperation are often undermined.
- Limited resources and capabilities: Not all countries have the same level of resources and capabilities to effectively respond to cyber threats, which can create disparities in international cooperation efforts.
International cooperation in cybersecurity is essential for addressing the increasingly complex and sophisticated cyber threats that we face today. By working together, countries can leverage their collective expertise, resources, and intelligence to enhance cybersecurity measures and protect against cyber attacks on a global scale.
Case Studies of National Cybersecurity Strategies
National cybersecurity strategies play a crucial role in safeguarding a country’s digital infrastructure and protecting its citizens from cyber threats. By examining successful case studies from different countries, we can gain valuable insights into the strategies implemented and their outcomes.
These case studies also provide valuable lessons that can be applied to other nations facing similar challenges.
United States
The United States has been at the forefront of developing and implementing a comprehensive national cybersecurity strategy. One of the key elements of their strategy is the establishment of the Cybersecurity and Infrastructure Security Agency (CISA) in 2018. CISA serves as the central agency responsible for coordinating and implementing cybersecurity efforts across various sectors.
The U.S. also emphasizes public-private partnerships to enhance cybersecurity resilience. This approach has resulted in improved incident response capabilities and information-sharing mechanisms.
Estonia
Estonia is often hailed as a pioneer in cybersecurity due to its strong emphasis on digital governance and cybersecurity measures. After experiencing a large-scale cyber attack in 2007, Estonia recognized the importance of cybersecurity and developed a robust national strategy.
Their strategy focuses on building a cyber-resilient society through initiatives such as secure digital identity, e-governance, and widespread cybersecurity education. Estonia’s proactive approach has made it a global leader in cybersecurity and a model for other nations.
Singapore
Singapore has also implemented a successful national cybersecurity strategy to protect its critical infrastructure and maintain a secure digital environment. Their strategy includes a strong regulatory framework, public-private partnerships, and a skilled cybersecurity workforce. The government has established the Cyber Security Agency (CSA) to oversee cybersecurity efforts and coordinate with various sectors.
Singapore’s strategy has resulted in a high level of cybersecurity maturity and resilience, making it an attractive destination for digital businesses.
Lessons Learned
These case studies highlight several key lessons for other nations developing their cybersecurity strategies. First, collaboration and coordination among different stakeholders, including government agencies, private sector, and academia, are crucial for effective cybersecurity. Second, investing in cybersecurity education and developing a skilled workforce is essential to address the evolving cyber threats.
Third, proactive measures, such as regular vulnerability assessments and incident response drills, help in building cyber resilience. Finally, continuous improvement and adaptation of cybersecurity strategies are necessary to keep pace with the rapidly changing threat landscape.
Final Wrap-Up
In conclusion, strategi keamanan siber nasional pdf is an essential tool for protecting nations in the digital age. By understanding its key components, leveraging international cooperation, and learning from successful case studies, countries can enhance their cybersecurity measures and mitigate potential threats.
Stay vigilant and stay secure in this ever-evolving cyberspace.
Answers to Common Questions: Strategi Keamanan Siber Nasional Pdf
What is cybersecurity strategy?
Cybersecurity strategy refers to a comprehensive plan and set of actions that a nation implements to protect its digital infrastructure from cyber threats, ensuring national security.
Why is cybersecurity strategy important for national security?
In the digital age, nations heavily rely on interconnected systems and networks. A cybersecurity strategy is crucial to safeguard critical infrastructure, sensitive data, and maintain the trust of citizens, businesses, and other nations.
What are the challenges and threats faced by nations in cyberspace?
Nations face various challenges and threats in cyberspace, including advanced persistent threats (APTs), data breaches, ransomware attacks, and state-sponsored cyber espionage. These threats can disrupt essential services, compromise national security, and undermine public trust.
What are the key components of a national cybersecurity strategy?
Key components of a national cybersecurity strategy include risk assessment, incident response planning, information sharing mechanisms, public-private partnerships, capacity building, legislation and regulation, and international cooperation.
How does international cooperation contribute to cybersecurity?
International cooperation fosters information sharing, joint efforts in combating cyber threats, harmonization of cybersecurity standards, and the establishment of frameworks for collaborative response to incidents. It strengthens global cybersecurity resilience and addresses transnational cyber challenges.